Vulnerability Assessment Reporting: Beginner's Guide
So you’ve been asked for a vulnerability assessment report. Maybe a board member asked for oversight. Perhaps it was one of your clients, partners, or auditors. Regardless of who raised the flag, the consensus is clear: You need to demonstrate how you’re managing your vulnerabilities.
No wonder, with over 25,000 CVE vulnerabilities recorded in 2022, if you want to be trusted by your partners and consumers, you should be able to prove that your organization does its best to avoid falling hackers' prey.
The thing is…where do you start? And how do you prove that you’re on top of your game? Read this guide to find out all you need about vulnerability assessment reporting and how to demonstrate to your customers and auditors that you’re in control of your security posture.
What is a Vulnerability Assessment Report?
A vulnerability assessment report details the security weaknesses discovered in a vulnerability assessment. It is your roadmap to a better state of security preparedness, laying out the unique risks you face due to the technology that underpins your organization. It also reveals how to overcome them without completely overhauling your core business strategy.
If you’re looking to secure your systems before hackers can exploit any underlying weaknesses, a vulnerability assessment is the right place to start. It’s an automated review process that provides insights into your current security state. It’s also the best security practice recommended by governments across the world, take a look at the UK, for example.
Why do you need a Vulnerability Assessment Report?
Your customer wasn't asking you to present vulnerability assessment results for fun. The reality is that no matter how hard you try to make your tech infrastructure impenetrable, it could have inherent weaknesses, and your board, customers, insurers, and auditors need reassurance that you’re on top of them.
If you’re handling customer data or acting as a supplier to other organizations, at some point in time you are likely to be asked to provide a vulnerability assessment report. Let’s look at some common scenarios of when you might need one and get you ready:
1. To meet compliance requirements
If the request for vulnerability reporting was made by your auditor, it is likely to be for compliance purposes. Many of the regulatory or compliance frameworks related to security and privacy, like SOC2, HIPAA, GDPR, ISO 27001, and PCI DSS, advise or outright require regular compliance scans and reporting. While others like GDPR simply state that good security practices must be followed, from which vulnerability assessment is often inferred.
2. To increase customer trust
Maybe the request for a vulnerability assessment report came from one of your customers? This is because weaknesses in your IT systems could affect their operations. With supply chain attacks on the rise, a vulnerability in a single company could leave the whole range of organizations paralyzed, as demonstrated by the infamous SolarWinds hack.
Even if you’re a small business, your customers may wish for confirmation that your IT security practices are tiptop before entrusting you with their data; and vulnerability reporting should be just the ticket.
3. Reduce cyber insurance premiums
If you're looking to insure your business against security breaches, your cyber insurance provider might be the one requiring vulnerability assessments reports. If you don’t want to run the risk of being denied your insurance payment or wouldn’t like to see your premiums rise, then you could benefit from supplying these reports regularly. Learn more in our guide to cyber insurance.
4. Build business resilience
Cyber security is a growing concern across many businesses, so chances are your board members want to take a better grip of their risk, before the lack of insights into vulnerabilities is turned into a much more serious business problem. With ransomware attacks regularly making headlines, having proper vulnerability management in place and presenting an “all clear” vulnerability assessment report, can give your business heads that needed peace of mind. We have a dedicated guide to vulnerability management metrics for more detail on exactly what you should be measuring.
What should a vulnerability assessment report contain?
Generally speaking, there is no unified vulnerability report template that has to be maintained by everyone, even for compliance purposes, unless you’re trying to adhere to PCI-DSS, which has its own specific requirements.
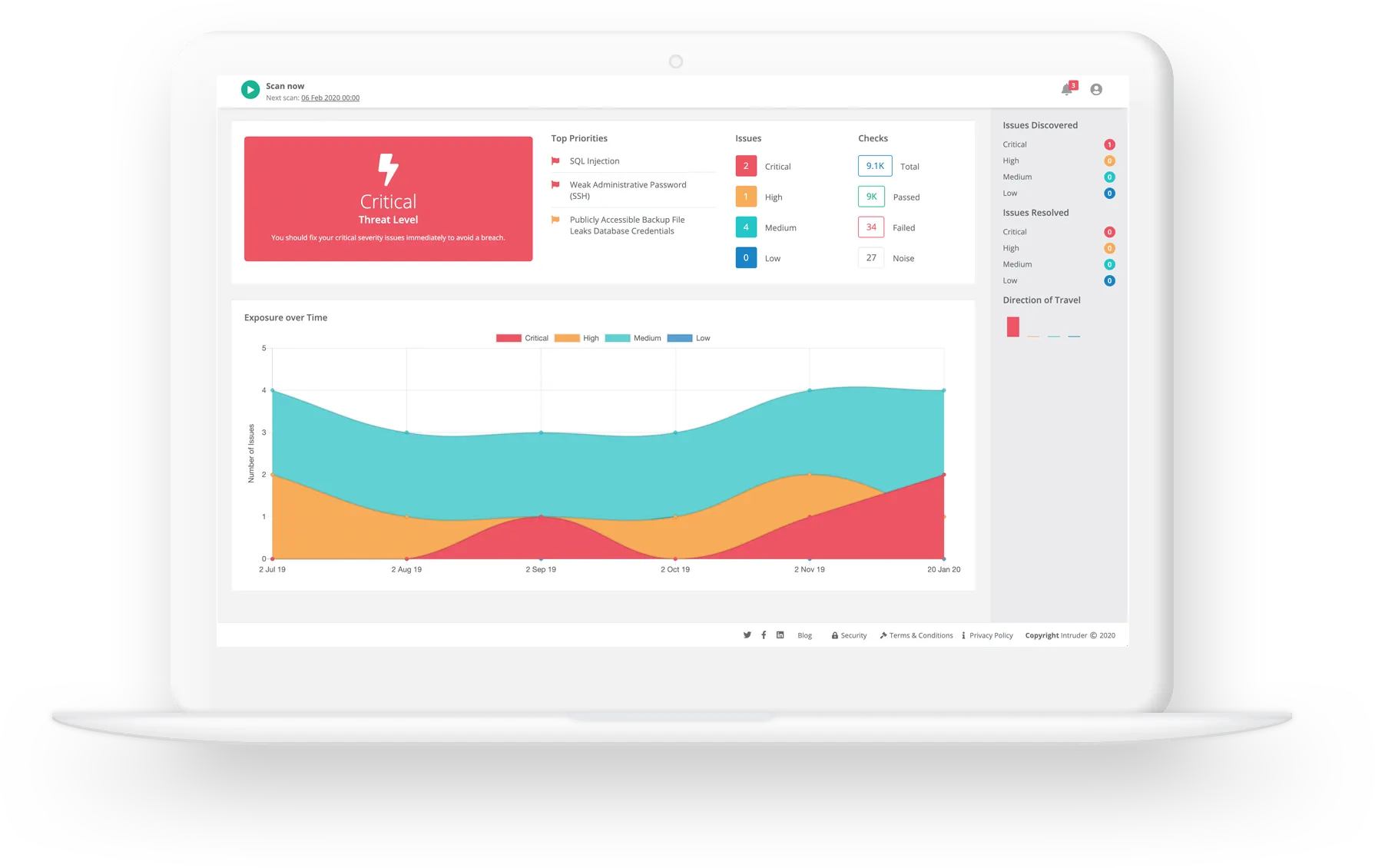
Typically, a vulnerability assessment report will show you the raw number of vulnerabilities detected in your systems at a point in time. Of course, in an ideal scenario, you want your vulnerability report to contain nothing = zero issues.
However, that’s rarely the case, as the world doesn’t stand still. Even if you’ve been relentlessly fixing your flaws for weeks, you can wake up tomorrow only to discover that more critical vulnerabilities were found. Wouldn’t it be great if you can still evidence to your management that you’ve been keeping your cyber flaws at bay, even if you’re in red now?
At Intruder, we use a cyber hygiene score which enables you to track the progress of your vulnerability management efforts over time, proving that your security issues are being continuously resolved in good time. Below, you can see our vulnerability report example.

Vulnerability assessment reports vs penetration testing reports
Most regulatory frameworks are very clear about what they need so be sure to check requirements for compliance to understand if you need to complete a vulnerability assessment or a penetration test.
Penetration testing, also known as pen testing, involves a trustworthy security researcher intentionally trying to break through services, password-secured networks, web apps, and other common technologies. As they go, they record precisely how they gained entry so that they can teach your IT admins how to close any existing backdoors and prevent similar gaps from opening in the future.
To give you a tip, if your security assessment needs to be done by humans, more often than not, you will require a “penetration test”. In other cases, a report produced by an automatic scanner should be sufficient. If you’re required to produce both vulnerability assessment and penetration testing (VAPT) reports, it should be clearly stipulated by whoever requested the report. You can learn more about the differences between penetration testing vs vulnerability scanning.
How to choose a vulnerability assessment provider?
After a requirement for a vulnerability assessment has been established, it is time to choose the right provider for your business.
It’s important to note that modern vulnerability assessment tools are becoming increasingly easy to use, so you don’t need to be a cyber security expert (or pay an external company) to start benefiting from one of them.
Before you start comparing individual vendors, first make sure you have a solid understanding of your technical environment and of the specific outcomes that the vulnerability assessment should present.
Why is this important?
Vulnerability assessment tools are not built the same; they check for different types of weaknesses, so you need to choose the best solution for needs. We’ve written a helpful guide that discusses vulnerability assessment tools in more detail.
When choosing your ideal scanner, you should consider:
- Features
- Checks performed
- Industry certifications
- Pricing
- Reporting
As we’re focusing on the reporting aspect in this guide, you might wish to choose a tool that gives you more flexibility in how you present your data to different audiences. After all, not everyone who reviews your vulnerability assessment reports needs the same level of detail.
Different reports for different needs – one size doesn't fit all
Although all versions of a given scan ought to cover the same fundamental data, it's usually wisest to tailor the content to distinct stakeholders:
1. The Executive Report
Managers benefit from graph views and composite cyber hygiene scores that clue them in on where they stand at any given moment. These documents are ideal for boards and C-suite leaders.
2. The Technical Report
Your IT team needs finer-grained data. These reports reveal how to apply the correct solutions to existing problems and sidestep subsequent mistakes.
3. The External Party Report
This style of vulnerability reporting is for everyone else. It lets compliance auditors, investors, and clients know they can depend on you to be a in control of your cyber security posture.
How often do you need to produce a vulnerability assessment report?
Vulnerability reporting isn't a once-and-done sort of affair – as is the case with vulnerability scanning. For maximum efficacy, you need to conduct regular, if not constant, comprehensive evaluations of your entire technology stack.
Why? Coming up clean on a scan is awesome, but don't be fooled into thinking that posting a security certificate on your website will deter serious bad actors. They won't stop searching until they find something they can take advantage of. Since new, publicly known risks surface by the hour, it's up to you to keep pace. This means running a vulnerability check every now and then won’t cut it.
Where can I get a Vulnerability Assessment Report from?
Effective vulnerability management requires expertise as well as the bandwidth to keep up with threats as they evolve. Here, at Intruder, we believe that the production of regular vulnerability assessments shouldn’t be a burden on your team – they’re extremely important in keeping your organization secure after all.
Intruder makes it effortless to start scanning continuously, without feeling overwhelmed by the results. Whether you're a massive enterprise or a fledgling startup, you can generate rapid reports, create compliance paper trails, stay secure, and communicate with employees and potential investors.
Intruder’s reports demystify complex security data to grant you a clear, jargon-free understanding of the risks you face. We even help you determine whether or not you need to fix specific issues and which might be false positives – something almost no other provider offers. Not only that but our high-quality reports are perfect to pass onto prospective customers or comply with security regulations, such as ISO 27001 and SOC 2.
Your future revolves around your security posture, and your security posture hinges on vulnerability assessment feedback. Shouldn't you be empowered to understand it?
With Intruder, setup only takes minutes, but it instantly puts you thousands of miles ahead of your current security position. Get started now with a free 14-day trial.
- Answering the question, “What is security testing?”
- Understanding the reasons to perform security testing
- Defining the scope of cyber security testing
- Knowing when to perform penetration testing

Written by