Security & Privacy + Security News
Mystery Surrounds “iCloud Hack” as Naked Celebrity Photos Leak
Posted on
by
Graham Cluley

You would have had to have been sleeping under a rock for the last day or two not to have seen the headlines about female celebrities whose naked selfie photographs have somehow slipped out onto the internet.
Most attention has been given to the candid photographs of Oscar-winning actress Jennifer Lawrence, model Kate Upton and recording artist Ariana Grande, but the truth is that about 100 other actresses, models and pop stars have had their private naked photographs shared widely on the internet.
The story first broke on Sunday, when links began to be posted on 4Chan image-sharing forum and Reddit alongside claims that suggested that iCloud had been hacked.
iCloud, of course, is Apple’s cloud storage and backup service – designed to make your life more convenient if you’re using Apple computers or iPhones, not to leak photos that you probably only intended your boyfriend or husband to see.
But many iPhone owners are possibly oblivious to the fact that every time they take a photo, it is invisibly and silently uploaded to iCloud in the background, entering your Photostream, meaning that it can be easily accessible from any other Apple devices you own.
That’s not necessarily always a bad thing.
I mean, lets face it, your photos are special to you and many of them will have significant sentimental value. The beauty of something like the Photostream or automatic iCloud backups of your data is that it doesn’t matter if you lose your phone or drop it in the bath, you won’t have lost your precious photos and other data.
But, of course, there might be ahem… some images that you wouldn’t feel comfortable being automatically shared anywhere, which you might want somewhat more paranoid and tighter control over because of their umm… content.
Because if a hacker managed to hijack your iCloud account, they could download all of your photos without ever having to gain physical access to your iPhone.
It’s important to stress at this point that there has been no firm evidence that hackers have exploited a security hole in iCloud to help them access the female celebrities’ accounts, but the theory has gained ground when proof-of-concept code was uploaded to Github this weekend that used cracking techniques to guess passwords for accounts.
The code, named ‘iBrute’, allegedly exploited a vulnerability in the Find My iPhone API, and was created by security researchers Andrey Belenko and Alexey Troshichev.
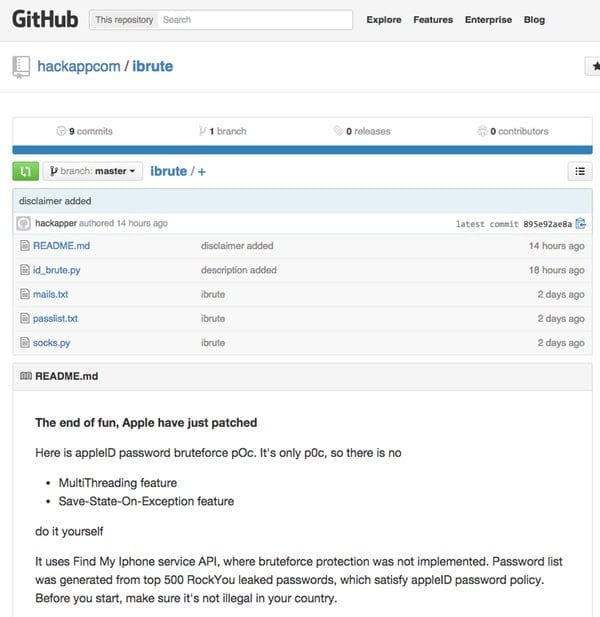
Although iBrute suggests it uses “brute force” to crack the passwords, it actually uses a dictionary attack – throwing the most popular passwords revealed by past data breaches to see if any of them stick against the wall.
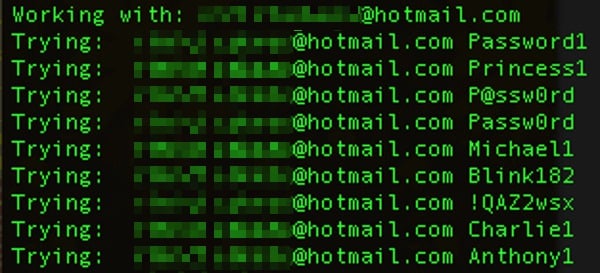
Regardless of whether it’s a brute force attack or a dictionary attack, the point is that Apple appears to have been failing to properly rate limit failed attempts to access an account.
Apple is said to have now fixed the flaw, which had meant that hackers could rapidly try thousands or even millions of possible passwords in rapid succession, to see which would unlock the door.
But what’s not known is if anyone else was aware of the flaw, or whether other security holes exist in iCloud’s security that could have allowed hackers’ access to private data.
This last weekend, Defcon in Saint Petersburg were given a presentation by Belenko and Troshichev, detailing weak points in iCloud security.
They confirmed that the Find My iPhone API failed to lock out users who failed to enter the correct password on multiple occasions, and that users’ iCloud security codes – which are separate from iCloud passwords – might also be vulnerable to brute force attacks as they are typically only four characters long.
In Troschichev and Belenko’s opinion, you should never rely upon a four digit iCloud security code – but choose something more complex instead.
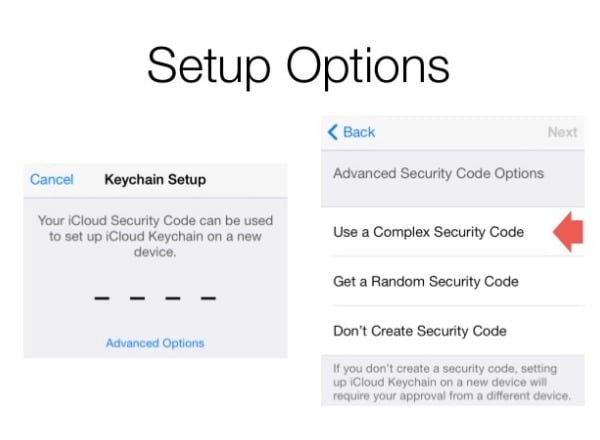
According to Apple iCloud support, “If you enter an incorrect iCloud Security Code too many times when using iCloud Keychain, your iCloud Keychain is disabled on that device [and] your keychain in the cloud is deleted.” You then have to access your account from another device.
Is it possible that the 100 celebrity victims could have had their accounts broken into in this way? To be honest, it’s hard to imagine that such a thing would be possible – and if it were true, it would throw Apple into a very poor light for not doing more to detect the suspicious activity against its servers.
The truth is that right now, we just don’t know. Other factors could have played their part including phishing, the unsafe reuse of the same passwords on multiple websites, or someone close to the celebrities leaking information or meddling with their online accounts.
RELATED: Did Jennifer Lawrence’s Naked Photos Leak Out Because She Told the Truth?
Unfortunately, one character in this story who could possibly shed some light, hasn’t got very much to say for itself at the moment.
Apple spokeswoman Natalie Kerris issued a curt response to journalists’ questions about the celebrity hack, which failed to dispel any concerns that it might be its own systems that were found lacking:
“We take user privacy very seriously and are actively investigating this report.”
Clearly with the launch of the long-anticipated iPhone 6 (and possibly an iWatch too?) just days away, Apple is keen not to have any bad news distracting attention.
Some things we can be certain of, however.
Make sure that you are using unique, hard-to-crack passwords for your iCloud account, and protect your account with two-factor authentication.
How to make your iCloud account harder to hack
Whether it is determined that a security hole helped hackers access iCloud accounts or not, it’s clear that other threats could put your online data and photographs at risk. For instance, phishing continues to be a thriving business, and it is becoming increasingly common to see iCloud accounts targeted just like online banks, PayPal, or social media sites.
To better protect your iCloud account, and prevent a hacker from accessing your backups, use two-factor authentication.

Two-factor authentication (sometimes called two step verification) makes life much harder for hackers attempting to hijack control of your accounts and devices, as it means they require more than just your username and password. They also need a one-time password (OTP) that is sent to your device itself.
In addition, you can set up a 14-digit recovery key that you can print out and keep in safe place. Apple suggests you keep the recovery key to regain access to your account, or if you ever lose access to your devices or forget your password.
Do you use Apple iCloud? Do you think Apple users take security seriously enough? Leave a message below sharing your thoughts.