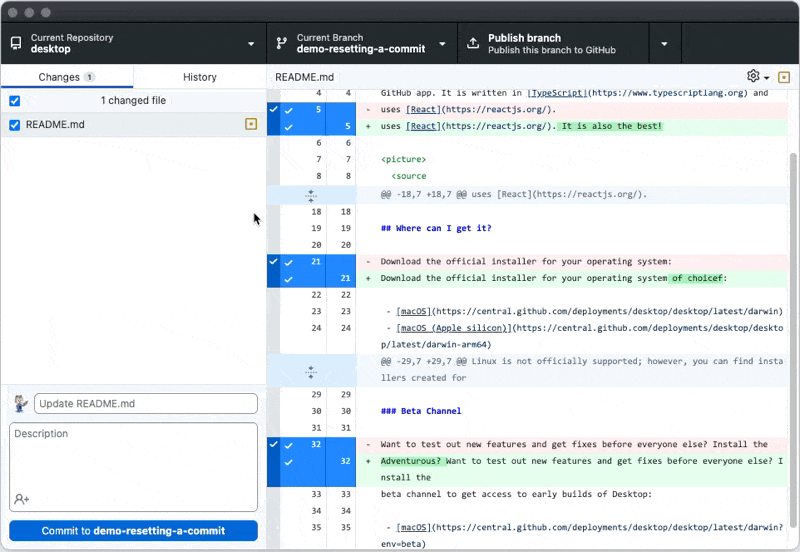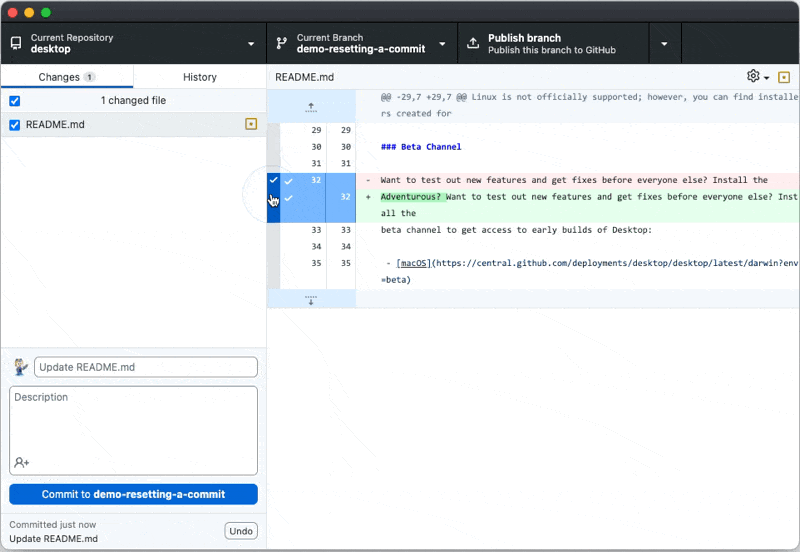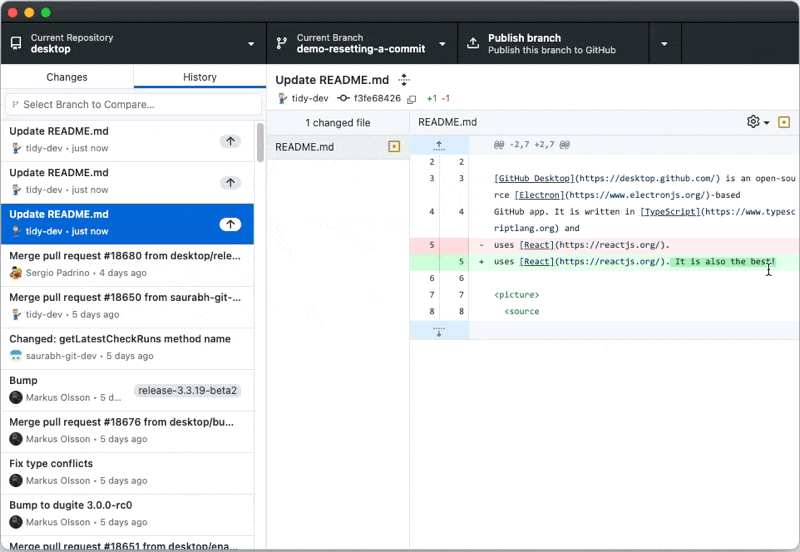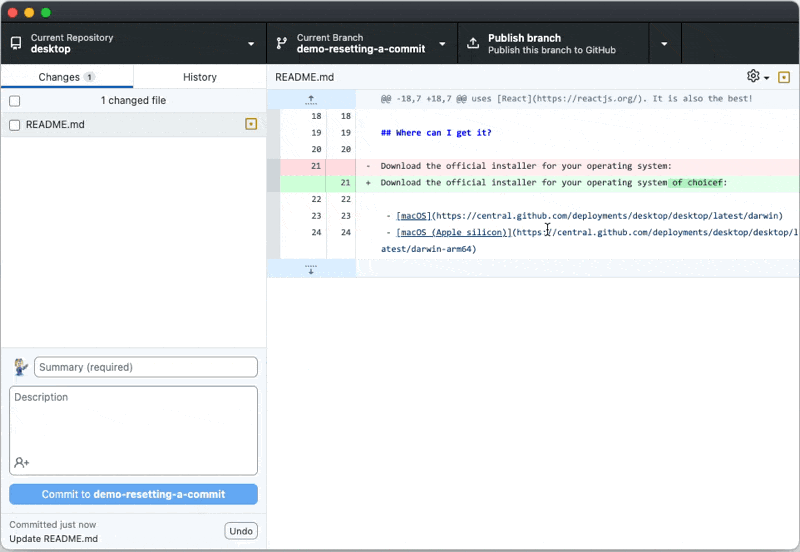
For security and convenience, we’ve updated how the account picker can be triggered during sign-in to an OAuth or GitHub Application. Some apps will see it all of the time, while all apps are able to trigger it manually.
Native apps (an app with a callback URI that doesn’t lead to an https:// destination) will now always receive the account picker to ensure that users get an opportunity to verify the application and change accounts if need be.
We’ve also added support for the standard prompt parameter with the select_account argument, which an app can provide during the OAuth authorization request to /authorize. This parameter forces the account picker to appear during authentication, interrupting what can otherwise be an instant authentication flow. We recommend using this parameter to better support multiple accounts at once in your app, if a user indicates they want to use another account in your app.
To force the account picker, append the following alongside your client ID and redirect URI parameters when you send the user to GitHub to sign in: &prompt=select_account.
As before, users with multiple signed in accounts will always see the account picker on each authentication.
To learn more about query parameters in the OAuth flow, see Authorizing OAuth Apps and Generating a user access token for a GitHub App.