Among the numerous hackers navigating the cyber world, a remarkable and intriguing group called Blue Hat Hackers catches our attention. But who are these enigmatic individuals, and what exactly is their role in the digital landscape?
Today, we spotlight these experts, these discrete heroes who work behind the scenes to ensure a smoother and safer digital experience for all of us.
This article will address the fundamental question: What is a Blue Hat Hacker? We will explore the hacking activities and skills defining these hackers and understand how they differ from White Hat Hackers.
Are you ready to embark on a journey through the unfamiliar world of Blue Hat Hacking? Let's get started!
What Is a Blue Hat Hacker?
The term Blue Hat Hacker is not widely recognized. Its curious origin is tied to Microsoft's annual security conferences, known as "BlueHat briefings." During these events, external researchers and hackers are invited to find vulnerabilities in Microsoft's products. The unofficial name "Blue Hat" is derived from the blue color featured on Microsoft employee badges.
Over time, this term has come to represent external security experts or ethical hackers who are brought in to identify potential threats within an organization's digital infrastructure before a product launch. Therefore, a blue hat hacker serves as the final gatekeeper, ensuring that a product doesn't have apparent or known vulnerabilities when it reaches the end users.
Microsoft BlueHat Conference
Established in 2005, the BlueHat conference remains a key event for cyber security professionals. Once again, in October 2023, researchers, industry leaders, offensive and defensive security experts came together to discuss the latest cyber threats.
Alternate Definition
Some individuals use the label Blue Hat to describe vengeful hackers or digital avengers who attack their enemies' computer systems to seek revenge for perceived or real injustices. Unlike red hat hackers, who are vigilantes, blue hat hackers are motivated by a sense of righteous indignation.
While this definition is somewhat common, it diverges from StationX’s perspective. We view the blue hats as a distinct and specialized group of ethical hackers, contributing to the cyber space in unique and valuable ways.
Want to follow the rules and take the ethical route? Take a look at our article Is Hacking Illegal? The Law and Ethical Perspectives
To shed more light on what makes blue hat hackers stand out, here is a side-by-side comparison with other hacking personas.
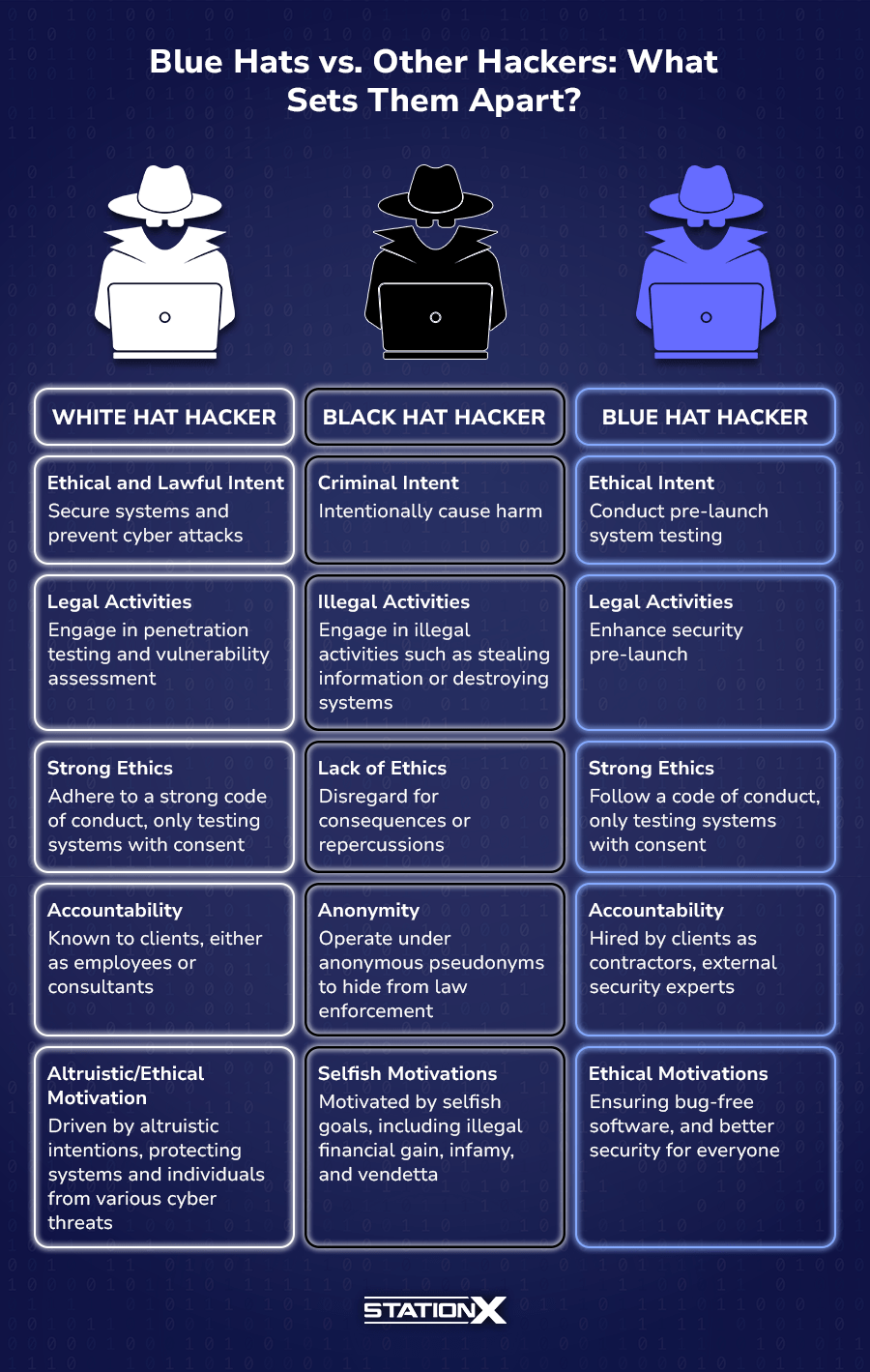
Curious about which hat suits you best? Check out our articles:
What Is a Red Hat Hacker? Time to Unravel the Mystery
What Is a White Hat Hacker? A Deep Dive Into Ethical Hacking
What Does a Blue Hat Hacker Do?
A Blue Hat Hacker’s tasks are typically similar to those of a white hat hacker, focusing on ethical hacking and security testing.
This category of hackers is employed by organizations to assess security measures, often before a new solution is released. Their primary mission is to uncover vulnerabilities using various methods and tools, including vulnerability scanning, security auditing, and penetration testing.
These experts not only find problems but also skillfully extract data from malware to create effective security defenses.
Here are some tasks specific to blue hat hackers:
- Ad Hoc Testing for Specific Projects: Blue hat hackers are often brought in for one-time or short-term engagements to test the security of a particular project or system.
- Independent Vulnerability Assessments: Blue hat hackers may perform vulnerability assessments independently, without direct affiliation with a specific organization, often to highlight security weaknesses and promote better security practices across various industries.
- Outsourced Projects Assessment: In cases where an organization outsources the development of a software application or system, these hackers may be called upon to assess the security of the outsourced project before integration.
- Product or Solution Validation: Blue hat hackers may evaluate the security of new products or solutions before their release to the market. This can involve testing software, hardware, or applications for vulnerabilities.
- Zero-Day Research and Exploitation: Blue Hat Hackers may focus on actively researching and exploiting zero-day vulnerabilities to discover and understand previously unknown security flaws in software or hardware. This is often done with software vendors to develop patches or mitigations.
Want to know if ethical hacking is your thing? Browse our article Is Ethical Hacking a Good Career Choice?
How Are Blue Hat Hackers Different From White Hat Hackers?
It's important to note that the lines between blue hat and white hat hackers can sometimes blur, and the terminology can be used interchangeably depending on the context and the nature of the engagement.
Both categories of hackers need authorization to perform their tasks. Whether you are a blue or white hat hacker, following these protocols is vital:
- Obtain approval: Always have written authorization from the organization or individual whose systems you are testing. For shared cloud environments, permission may also be required from the applicable service providers.
- Define Scope: Clearly define the scope of the assessment, specifying which systems, networks, and assets are to be tested during the engagement.
- Respect privacy & confidentiality: Respect privacy and confidentiality. Don’t access personal information or share sensitive data, including any other data collected during the assessment, with unauthorized parties. A non-disclosure agreement is usually signed beforehand.
- Responsible Testing: Avoid causing harm to systems, computer networks, or data during your assessment. Do not exploit vulnerabilities beyond the point of identifying them.
- Continuous Communication: Maintain open communication with the organization throughout the assessment, per the defined procedure, to provide updates, address any emerging issues, or report your findings.
Note that the key distinction between blue hat and white hat hackers lies in their engagement, motivations, and relationships with the organizations they work for.
What Skills Do Blue Hat Hackers Have?
A diverse skill set is indispensable to excel as a Blue Hat Hacker.
Apart from understanding computer systems, networks, and the latest cyber threats, proficiency in the following areas is crucial:
- Penetration Testing: To operate as a blue hat hacker, you need this skill to simulate cyber attacks successfully and identify vulnerabilities in systems, networks, and applications.
- Web App Testing: To scrutinize web applications for vulnerabilities, like XSS and SQL injection, ensuring the security of web services and user safety.
- Software Testing: Expertise in software testing allows blue hat hackers to pinpoint code vulnerabilities, enhancing system security and safeguarding software from exploitation.
- Reverse Engineering: Blue hat hackers analyze software, hardware, and protocols to understand their architecture and inner workings. This skill helps them find hidden security vulnerabilities and develop strategies to defend against emerging threats.
- Exploit Development: Blue hat hackers create new hacking techniques and test attack tools to demonstrate how vulnerabilities can be exploited. This skill empowers them to address sophisticated cyber threats and improve security proactively.
Explore this episode of the Microsoft BlueHat Podcast, where they delve into vulnerability detection, the benefits of crafting custom tools for new projects, and the approach for uncovering logic vulnerabilities.
Why Are Blue Hat Hackers Important?
Amidst the surge in sophisticated cyberattacks, the cyber space has become a battleground. Within this cyber chaos, blue hat hackers play a pivotal role in fortifying the digital landscape, protecting companies data from threat actors, and providing end-users a secure and seamless experience.
By focusing solely on a software product or system, they bring meticulous precision to vulnerability detection.
Other factors underline the importance of blue hat hackers, including:
Conclusion
The term Blue Hat Hacker undoubtedly unveils a unique aspect of ethical hacking that isn’t widely known.
Although they may not often make headlines or be the topic of everyday conversations, these ethical hackers’ contribution to our digital world is undeniable. So, the next time you click, browse, or swipe on your favorite apps without a glitch, remember that it’s maybe thanks to the blue hats who have worked behind the scenes to ensure everything works just fine.
Our course selection and the StationX Accelerator Program provide a comprehensive training service and personalized mentorship, equipping you with the essential skills needed to enter the hacking world. Check them out!
Frequently Asked Questions
Level Up in Cyber Security: Join Our Membership Today!










why am i getting adverts for how i hack ppl like what